UNIX COMMANDS:
format:
machine:current directory user$ command -flag
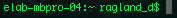
Prompt:
shows the user
shows that it is ready for input
user= $
super user= #
Sudo: becomes the super user for the command.
Command: the program you want the machine to run
flags: parameters for the program, to specify a more precise action.
Wildcards: * means all, allowing to perform functions on specific files.
Control+C, Control +Z, q, Esc, exit: used to exit a running process and return to the prompt.
say:
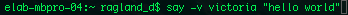
this function makes the computer speak.
flags such as -v allow you to pick a voice.
This can be used in conjunction with SSH for some fun pranks.
In addition, it can be used to read out loud a text file, such as all of Moby Dick.
osascript:
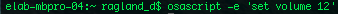
Apple Script allow for more direct control with the operating system through Open Scripting Architecture.
Custom commands specific to Apple allow for command line use of complex programs.
The flag -e '' allows you to edit and create scripts.
here is an example script: sudo osascript -e 'tell application "Finder"' -e 'activate' -e 'display dialog "It is pitch black. You are likely to be eaten by a grue." buttons "OK." with icon note' -e 'end tell'

here is an example script: sudo osascript -e 'tell application "Finder"' -e 'activate' -e 'display dialog "It is pitch black. You are likely to be eaten by a grue." buttons "OK." with icon note' -e 'end tell'

man:


Manual allows a user to see a reference page for a command they are unfamiliar with.
It is helpful to press Apple+N to open a new window first, so one can use the terminal with a reference side by side.
fsck -yf:

File system check yes force performs a system check on the files inside the computer.
This can make the system a lot faster, as it fixes broken links and repairs directories for example.
It also can be used in single user mode to fix broken computers without a GUI.
It also can be used in single user mode to fix broken computers without a GUI.
last:
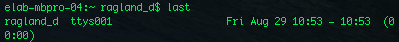
Last shows who has logged in last.
This is useful if someone is SSHing into you.
This is useful if someone is SSHing into you.
who:
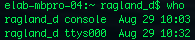
Who shows who is logged in right now, which should only be you.
w:

w is who with more features such as where people are logging in from, etc.
whoami:
whoami:

Whoami tells you who you are logged in as.
Exit is used to exit a process or program.
Alternatives include Control+C, Control +Z, q, and Esc.
Alternatives include Control+C, Control +Z, q, and Esc.
history:
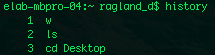 History shows your command history, making debugging useful.
History shows your command history, making debugging useful. It also serves as a log, if someone is trying to hack you.
In addition, the UP arrow key fills in the command prompt with previous commands, allowing one to perform similar functions with minimal typing.
If one ever has to perform the same command more than once however, a script would be more useful.
In addition, the flag -c clears the history.
ls:

ls -la
 List lists the files in a directory.
List lists the files in a directory.
The flag -la lists all files, and their attributes.
For example, the left letters show the permissions of the files for different users, with r being read, w being write, and x being execute.
The first letter, d, means that it is a directory. The next three are owner, followed by group members, and user.
Next are the owner and group, followed by how much memory each file takes, its modification date, and finally, its name.
It even lists important hidden files with a ..
These files are hidden because they are usually important system files, but must still have a function to see them for administrative purposes.
This command is significant because files are central to the UNIX system, and many of the configuration files are text files that can be read by humans.
These files can be edited with simple programs such as vi, vim, and nano.
Other flags include
-a: all
-l: long format
-f: do not sort
-R: recursively list
-t: sort by modification time
-h: print in human readable memory formats.
pwd:
 List lists the files in a directory.
List lists the files in a directory. The flag -la lists all files, and their attributes.
For example, the left letters show the permissions of the files for different users, with r being read, w being write, and x being execute.
The first letter, d, means that it is a directory. The next three are owner, followed by group members, and user.
Next are the owner and group, followed by how much memory each file takes, its modification date, and finally, its name.
It even lists important hidden files with a ..
These files are hidden because they are usually important system files, but must still have a function to see them for administrative purposes.
This command is significant because files are central to the UNIX system, and many of the configuration files are text files that can be read by humans.
These files can be edited with simple programs such as vi, vim, and nano.
Other flags include
-a: all
-l: long format
-f: do not sort
-R: recursively list
-t: sort by modification time
-h: print in human readable memory formats.
pwd:
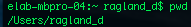 Print working directory shows one where they are inside the file directory tree, which is immensely helpful when navigating without a GUI.
Print working directory shows one where they are inside the file directory tree, which is immensely helpful when navigating without a GUI. cd:
cd ..:
cd /:

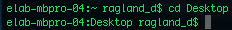
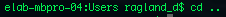
Change directory allows one to travel between folders within the file tree.
cd .. moves one up a directory.
cd / moves one to the root directory.
Relative and absolute pathways are also utilized here, as cd.. is relative, while cd /Users/dragland_r is absolute.
find:
 find searches the local directory for whatever you want, and can be used in conjunction with wildcards to be truly effective.
find searches the local directory for whatever you want, and can be used in conjunction with wildcards to be truly effective. locate:
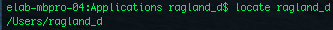 Locate finds a file that is anywhere in the computer, as long as it has been indexed.
Locate finds a file that is anywhere in the computer, as long as it has been indexed. ssh:
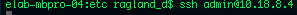

Secure Shell allows for remote login into a computer, as long as you know the machine IP, user, and corresponding password.
This opens up their terminal inside yours, so that whatever you type occurs on the other machine.
This can be used in conjunction with an X11 utility, allowing one to boot up a graphical user interface remotely.
The reason SSH is secure is that it used RSA keys to ensure identities.
For example, this is what happens when the keys don't match.
This opens up their terminal inside yours, so that whatever you type occurs on the other machine.
This can be used in conjunction with an X11 utility, allowing one to boot up a graphical user interface remotely.
The reason SSH is secure is that it used RSA keys to ensure identities.
For example, this is what happens when the keys don't match.

nano:
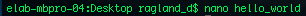 Nano is a simple yet powerful text editor that can be used within the terminal.
Nano is a simple yet powerful text editor that can be used within the terminal.  when one is finished, you press command+O to save it, and command+X to return to the prompt.
when one is finished, you press command+O to save it, and command+X to return to the prompt. less:
 Less is one example of a text viewing utility.
Less is one example of a text viewing utility. 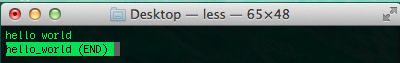 q is used to quit.
q is used to quit. more:
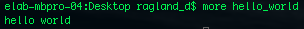 More is another text viewing utility, and actually shows the text within the prompt.
More is another text viewing utility, and actually shows the text within the prompt. It is also an example of the creativity of computer geeks.
cat:
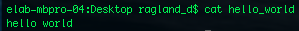 Concatenate takes a text file and organizes the data within.
Concatenate takes a text file and organizes the data within. It also prints within the terminal prompt.
tail:
 Tail is another text viewing program, but it rather only lists the last 10 lines of a file, which is useful for updated logs.
Tail is another text viewing program, but it rather only lists the last 10 lines of a file, which is useful for updated logs. touch:
 Touch can be used to create a new empty file, and also change its modification date.
Touch can be used to create a new empty file, and also change its modification date. The flag -t 200701310846.26 achieves this.
mkdir:
 This function makes a directory, adding to the file system tree.
This function makes a directory, adding to the file system tree. rmdir:
 This function removes directories.
This function removes directories. This is different from the file removal command, as it is safer to have separate commands than to accidentally delete entire directories.
cp:
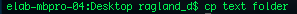 Copy creates a second version of the file in a specified directory.
Copy creates a second version of the file in a specified directory. mv:
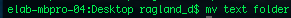 Move moves the file, meaning that there is still only one copy.
Move moves the file, meaning that there is still only one copy. It also can be used to rename files by not having a /.
rm:
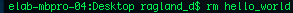 rm removes files, and can be used with wildcards to achieve extremely specific functions.
rm removes files, and can be used with wildcards to achieve extremely specific functions. Rm -rf *.* deletes everything.
top:
 Top lists the running processes in real time.
Top lists the running processes in real time. It also has useful data such as the process id, the percent of CPU used, the time, the port, and the memory used.
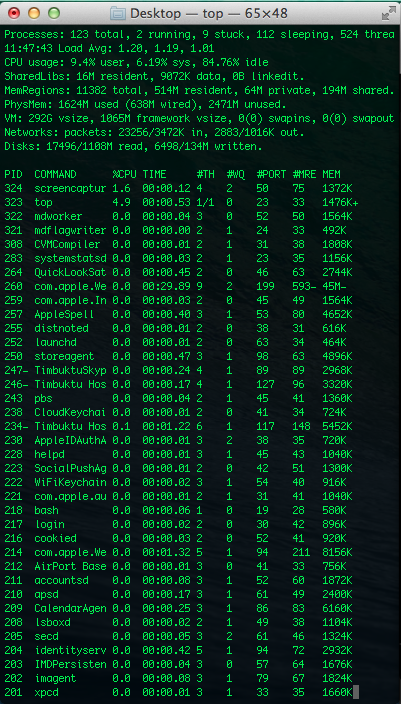
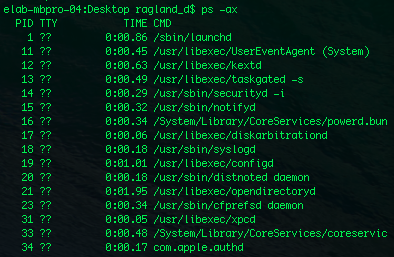
ps:
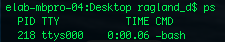 Process status also lists the currently running processes.
Process status also lists the currently running processes. The flag -ax lists even more.
kill:
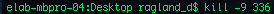
After one gets the process ID of a process, they can use kill to terminate the process.
The flag -9 can be used to force terminate if the program is fighting back.
The flag -9 can be used to force terminate if the program is fighting back.
open:
 open opens files, allowing one to switch back to the GUI for more specific tasks.
open opens files, allowing one to switch back to the GUI for more specific tasks. It can also open urls, like this : open https://www.youtube.com/watch?v=dQw4w9WgXcQ
This can also be used with wildcards, so the command open *.app would open every single application installed, each with a unique PID, making it a particularly gruesome yet entertaining SSH prank.
shutdown:
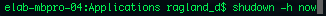 shutdown powers off the machine, and often requires superuser permissions.
shutdown powers off the machine, and often requires superuser permissions. Flags such as -h, -r, and +5 tell the system to halt, restart, and do either after an amount of time.
Comments
admin
Sep 1, 2014
Davy,
This is truly excellent, thanks for taking the time on this.
aloha
b